
Systems Engineering & Design
Implementation of sound engineering principles to complex projects is critical to reduce risk and thereby lay the foundation for the highest return on investment – particularly when employed in the design, development, testing, and maintenance of software systems.
A sound engineering framework, when executed consistently and properly, will result in the highest quality result at the least initial cost. Moreover, dividends will continue in the years to follow resulting from reduced maintenance costs.
Unfortunately, systems engineering practices are often significantly downplayed, or overlooked, particularly in the agile arena where scrum teams are under pressure to produce working software within the short time frame of each sprint.
The additional effort and resources necessary to employ a comprehensive set of scientific principles and procedures will, as supported by multiple studies, be recovered through increased efficiency of the production process, improved quality and stability of software code, minimized cost of system implementation and use, and decreased maintenance costs.
Synergy Group IT employs engineering driven principles through processes and techniques which benefit all IT projects without regard to development methodology used. Each will seamlessly dovetail with principles and standard practices of Rapid Application Development, Lean, XP, Scrum, and DevOps as well as most other development methodologies. Applied processes and techniques include: test-driven development utilizing automated unit testing and an automated acceptance test framework, enforcement of good coding practices, appropriate use of refactoring, embedding security into code, maintaining good version control, and adherence to project work scope.
Test-Driven Development. The importance of structuring the coding process to adhere to the tenants of Test-Driven Development (TDD) cannot be overstated. At its most basic, TDD entails integrating automated unit testing into the coding process. Comprehensive unit tests, designed to capture logic errors and ensure all acceptance criteria are addressed, are written in conjunction with the actual code. Use of an automated testing run commiserate with each build ensures that each unit test remains in a "green" status - indicating that the test criteria has been appropriately addressed via clean code - as local development progresses.
Setup of an automated acceptance test framework on the integration server is key to leveraging each test as new code segments are integrated into the main development branch. Any conflict between newly integrated local code and the main branch is immediately identified enabling resolution before code is put into production.
Good Coding Practices. Enforcement of good coding practices across development teams is key to producing higher-quality products that are easier to maintain, update, and upgrade. Best practices, rooted in “tricks of the trade” employed by developers over the years to achieve these very results, include:
-
Uniform Style & Good Structure
must be achieved by adherence to a number of principles/conventions including appropriate use of comments,
descriptive naming conventions, and uniform formatting as discussed in sections to follow.
Other important considerations include:
- An emphasis on writing self-explanatory code. Readable code is always preferable as it is easier to review or enhance than code written with an emphasis on optimization.
- Adherence to the KISS principle which postulates that a simple and straightforward approach to solving a problem is better than a more complicated and complex approach. In the context of software code: simple and straightforward code is cleaner, easier to understand, and less likely to have bugs than complicated and complex code.
- Adherence to the Interface Segregation principle which states that many client-specific interfaces are better than one general-purpose interface.
- A religious adherence to producing reusable code which requires each unique task to be represented by a single method or function across a software system. Several principles underlie this objective most notably Separation of Concerns which postulates that each responsibility or task should be addressed by a unique function, class or component.
- Comments substantiative and detailed enough to provide explanation and context of code snippets. These annotations are key to understanding the logic underlying implementation of the functionality of all but the simplest of code. Information conveyed improves the efficiency and effectiveness of the peer review process, provides a necessary roadmap for refactoring, and provides context for developers tasked with making future enhancements.
- Naming Conventions - applied consistently - make code more readable and reduce the risk of confusion. Whether Hungarian Notation, Multiword Delimited, or another convention is used, variable names must be self-explanatory clearly representing the underlying data each stores. Class and Function names should be descriptive with the purpose of each easily distinguished.
- Formatting, employed uniformly, reveals the structure of code. Indentation and formatting, through the use of tabs, uniform spacing, white-spacing, maximum line length or wraps, and breaks, ensure that code is well organized and as such easily readable.
- Peer Review to supplement unit testing by providing a fresh set of eyes for detection of errors in logic or failure of code to adequately address all aspects of acceptance criteria. Determination of the need for refactoring is a further benefit of this best practice. Worth noting, peer review is part and parcel of the Agile practice of paired programming.
- Portability achieved through the use of parametrized configuration variables permits code to properly function when moved from one environment to another – most typically from development to production. Hard-coded literal values prohibit ease of movement as changes in values must be made manually increasing costs and introducing risk of error. Instead, configuration variable values must be controlled through database files, flat configuration files, or application servers.
- Merge Requests (aka Pull Requests) are a critical component of larger development projects. A Merge Request initiates a process whereby code developed locally, using a fork of the main repository, is reviewed and tested before being merged into the main repository. This process ensures a thorough Peer Review of new or enhanced code and relies heavily on adequate Comments, descriptive Naming Conventions, and consistent Formatting. As well, use of an automated acceptance test framework updated with current unit test criteria is critical to the effectiveness of this best practice.
Refactoring. Unique to the IT arena, the verb refactor refers to the systematic process of rewriting source code to improve its readability, reusability, or structure – in essence to bring code into conformance with the tenants of Uniform Style & Good Structure. No new functionality is added nor underlying behavior changed. Refactoring may result from initial review of code by the author or from peer review. In conformance with the Open-Closed principle, refactoring should typically be avoided.
Embedded Security. Essential to all aspects of development, security is one of the software engineering basics. Embedding security into source code is critical as the application layer, as estimated by Gartner, contains 90 percent of all vulnerabilities. Code must be engineered such that it is not vulnerable to malicious attack. Best practices require addressing security early in, and throughout, the software development lifecycle based on an up-to-date understanding of security threats and techniques to address each.
Adequate Version Control. Execution of best version control practices is a necessary insurance policy to control potential damage inherent from injection of substandard code into a production environment. Whether implemented via a proprietary source code management tool, an open-source system, or a home-grown alternative, use of a version control system capable of enabling a timely rollback if required is critical to any enterprise.
Well Defined Project Work Scope. Integral to the definition of any project is an agreed upon Scope of Work on which timelines and budgets are based. Unlike the Waterfall model, all modern project methodologies allow for controlled changes in project scope. That said, engineering practices must be employed to ensure resources are expended to generate code solely to meet agreed upon acceptance criteria. It is not uncommon for programmers to add features to applications based on a perceived need beyond those assigned – the very definition of scope creep. Project management practices, some encapsulating other software engineering techniques such as Peer Review, must ensure focus of time and resources remain on building reliable, effective code within the scope of work.
(See Agile Methodologies: Engineering Essentials regarding the critical need, and benefits, of using each of these Software Engineering practices as well as a breakout of Agile specific processes and techniques.)
The Synergy Team
Implementation of well-defined scientific principles and procedures to deliver an efficient and reliable software product requires a project to be thoroughly managed by engineers having varied qualifications. Dependent upon the nature, size, and complexity of a given project, Synergy’s engagement team will include one or more of the following specialists:
- Quality Assurance Engineer
- Security Engineer
- Front-end Engineer
- Back-end Engineer
- Data engineer
- Development and Operations (DevOps) Engineer
Systems engineering enables a complex project to be managed from a proactive perspective rather than reactive one thereby minimizing risk to the fullest extent. The cost of post-implementation failure, often incalculable, is circumvented as data persists secure and uncompromised. In safety-critical areas such as medicine and mass transportation, lives are not needlessly put in jeopardy. Through the use of structured software engineering issues can be anticipated, addressed, and eliminated - thereby preventing loss - whether a project is focused on converting a legacy system or on addressing newly discovered system requirements.
Custom Engineered Applications
Synergy has developed a myriad of Custom Software Solutions that enable clients to implement and support a broad spectrum of strategic objectives. Our solutions include comprehensive enterprise-wide systems as well as smaller sub-systems that provide functional support at a departmental level. These systems have been implemented across a diverse group of commercial enterprises, associations and not-for-profits, pension funds, and labor unions and their affiliates.
Several of Synergy's Custom Systems have continued in use since the late 90's; over time each has been migrated across several platforms as well as enhanced to meet evolving requirements. Our clients' leverage of their initial IT investment results from Synergy's initial comprehensive Analysis and Design - the foundation of robust and extensible systems.
Development & Integration Representative Cases provides exhaustive documentation of Custom Engineered Applications that Synergy has developed over 30+ years of serving clients across multiple industries.

Project Management
Synergy provides comprehensive project management services which address the full systems development life-cycle. Many projects are focused on discrete elements of the broader life-cycle however. Each engagement is staffed to provide the level of expertise required to ensure a successful systems solution.
Many organizations do not retain dedicated development personnel on staff as, given their business needs, such resources are cost prohibitive; these corporations, agencies, or not-for-profits require Synergy Group IT to perform a full spectrum of project tasks. Where in-house development expertise does exist – and is available to a given project – the engagement scope is tailored to ensure that Synergy staff complement internal resources for specific, specialized tasks. Whether provided by client staff or by Synergy personnel, each project must have the experience and expertise to ensure that the project is successfully initiated, developed, and implemented.
A broad project management skill set is required to provide the expertise necessary to develop, promote, and synthesize input from – and cooperation among – individuals and groups both internal and external to an organization. Our project managers and business analysts have educational backgrounds in Accounting, Finance, Management, and/or Marketing. All have developed project skill sets based on experience on engagements across a wide variety of corporate, association, and not-for-profit clients.
PM Case Studies provides a sampling of project management engagements provided to our clients,

Systems Analysis
Definitions of Systems Analysis across sources vary to differing degrees. The essence of this discipline as it pertains to the information technology development arena is found in Merriam-Webster’s definition depicted at right.
Over time, distinct frameworks have evolved within academia. Through years of experience working across numerous business sectors as well as within the labor community, and with defined benefit pension plans, Synergy has honed and successfully applied the approach outlined below.
Comprehensive Determination of Goals & Objectives
Definition of a business unit’s goals or purposes is fundamental to effective systems analysis. A thorough review of available documentation provides the foundation of this phase. Building upon results of this initial effort, an interrogation of appropriate stakeholders is undertaken to delve deeper into and confirm, information previously collected; through this effort, additional business objectives not found in available documentation are often discovered.
Evaluation of Existing Practices
The second phase of systems analysis comprises an in-depth evaluation of the degree to which each objective is supported by existing practices; a key focus of this component is making a determination of the efficiency and effectiveness of methodologies & techniques employed. Use of benchmarking, as well as other scientific measurement tools, is often necessary to substantiate and support an indepth evaluation. This approach requires a comprehensive review of inputs, processes, and outputs of existing IT systems revealing the manner and method used to automate a subset of overall policies and procedures. Such examination may expose additional business goals and objectives not exposed in the first phase of analysis.
Revamping and Enhancement of Existing Procedures
Subsequent to, or in parallel with, evaluation of existing practices, the analysis team will determine changes and/or enhancements to existing policies or practices which do not address defined goals and objectives. This step may
(The team may determine that the existing processes and workflow are fundamentally flawed and ineffective – are in effect dysfunctional - to the degree that changes cannot be made to enable efficiencies sought through further investment in automation to be achieved. In such a case, a recommendation will be made to executive leadership to curtail the systems analysis project and initiate a more comprehensive Business Process Re-Engineering effort. All work product of the analysis team will be preserved to support a BPR initiative.)
However, when the structure of business units and internal departments provides a strong foundation for effective workflow, the analyst will submit recommendations for improvements to existing policies and procedures, and for fundamental changes or enhancements to the manner and methods by which automated policies are effected. Finally, recommendations will be made regarding potential enhancements to current systems to automate additional processes.
Output and Recommendations
It is imperative that the analysis team produce unambiguous documentation encompassing the comprehensive set of “operations and procedures for accomplishing [the unit's goals and purposes] most efficiently”; doing so will provide a roadmap for next steps which will utilize the results of systems analysis project.
High level recommendations must reference details of changes in policies and procedures necessary to effect increased efficiencies and quality of business unit output. Additionally, recommendations typically address areas of improvement in project structure and implementation which may be of use to other projects initiated by stakeholders. For example, it is often the case that suboptimal executive level support for a project leads to inefficient and difficult implementation; attention of such a situation can ensure that it is addressed early in any follow-on project.
Systems Analysis and Agile
Systems analysis is necessary at the onset of all IT development projects including those structured around an agile method. Output of a successful analysis will provide a roadmap which when deconstructed will suggest an effective breakdown of an overall project effort into sprints of appropriate size and scope.
Synergy uses variations of the systems analysis process outlined to structure engagements in Project Planning, Data Analysis, Capability Analysis, Risk Measurement, Operational Research & Analysis, and Quality Assurance.
Systems Analysis and Conversion of Legacy Systems
Comprehensive analysis is critical at the onset of any legacy system conversion. It is imperative that the development team fully understand inputs, processes, outputs, and interfaces before initiating a conversion project without regard to whether the effort includes significant system re-design. The adage frequently displayed in Pottery Barn retail outlets - "You break it, you own it" - is a fundamental truth of legacy systems conversion.
Engagements Requiring an Approach Analogous to Systems Analysis
Synergy has engaged in other projects akin to systems analysis structured upon variations of the systems analysis process outlined. Undertakings include: Operational Research & Analysis, Risk Measurement, Quality Assurance, Data Analysis, Capability Analysis and Project Planning.
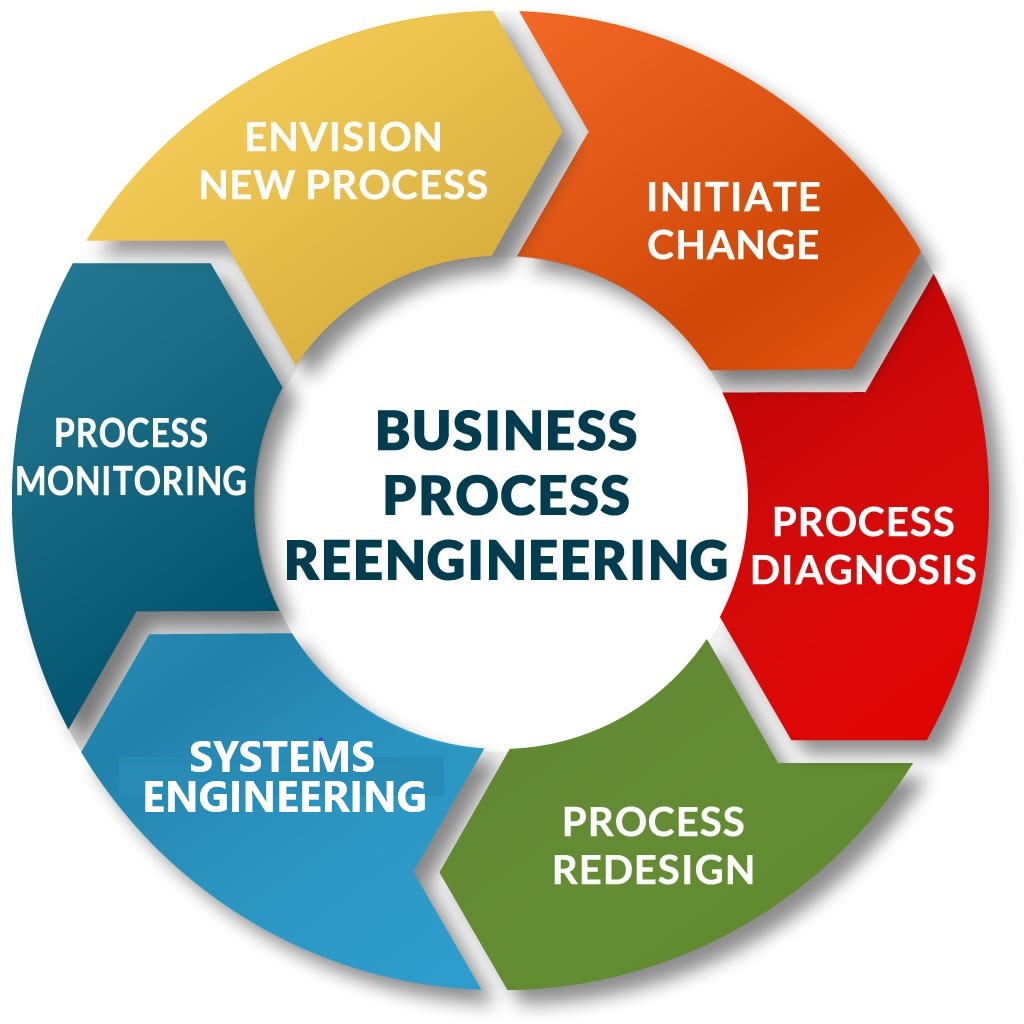
Business Process Re-Engineering
The underlying premise of Business Process Reengineering (BPR) holds that maximum efficiency of operations within an organization cannot be achieved simply by automating dysfunctional processes many of which were not consciously designed but evolved of necessity over a period of time. To adapt the adage most often attributed to Michael Hammer, “Using technology to make a horse faster by ‘upgrading’ it with lighter horseshoes makes little economic sense; a more prudent use of technology is to build a car - replacing the horse while providing infinitely greater functionality.”
(Michael Hammer first proposed the conceptual underpinnings of Business Process Reengineering; the principles which would define the field were codified in Reengineering the Corporation, co-written with James Champy.)
A second postulate of BPR argues that the pursuit through innovation of increased quality of products and services will permit traditional objectives to be achieved to a higher degree using fewer resources. For example:
- existing internal controls (checks and balances) can be enhanced
- existing costs can be reduced significantly
- growth and expansion can be more profitable as automation of re-engineered processes changes the linear trajectory of variable unit cost of product sold or service rendered
BPR History & Successes provides an in-depth review of BPR's historical roots as it pertains to the dramatic results which accrue to organizations that redesign, reorganize, redevelop, modernize, and streamline workflows. It features the dramatic results achieved by Ford Motor Company from its radical transformation of its Goods Acquisition Process.
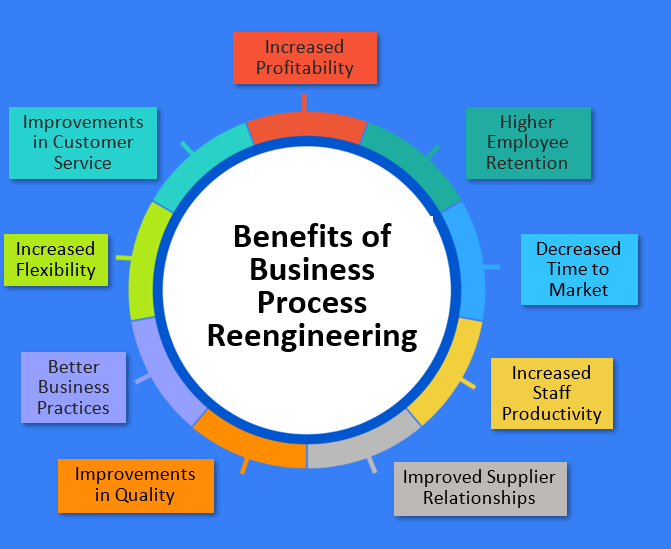
Synergy's Experience & Expertise
Our expertise in the field of Business Process Reengineering is both broad and varied. Synergy has performed BPR across several industries as well as labor unions and defined benefit pension plans. Responding to technological changes as well as changes in its internal political environment, one client performed BPR a second time – 15 years after the first - to revamp the operations and workflow of its Membership Processing and Services department.
Synergy clients have reaped many of benefits depicted at right through an investment in bringing about radical change to their historical workflow. These advantages include:
- Increased Profitability from dramatic reductions in cost as well as revenue growth
- Higher Employee Retention from empowering employees and improving their satisfaction
- Decreased Time to Market from leaner and more productive processes leading to reduced cycle times
- Increased Staff Productivity through eliminating obsolete inefficient procedures and unnecessary management overhead
- Improved Supplier Relationships resulting from cost savings to suppliers provided through the use of digital interfaces
- Increased Quality of services due to dramatic improvements in customer service
- Higher Product Quality through the use of system enabled lean manufacturing with automated quality checks
- Better Business Practices emanating from dramatic improvements in business processes as measured by quality and customer service
- Increased Flexibility to Power Growth resulting from bending the curve of variable costs as related to revenue increases
Following are details of several Business Process Reengineering engagements which demonstrate Synergy’s skill in the field both as it pertains to achieving fundamental changes to operations and related workflow as well as being perceptive to, and mitigating any effects of, the stresses of organizational change on client employees.
Links below detail two Business Process Reengineering engagements which demonstrate Synergy’s skill in the field both as it pertains to achieving fundamental changes to operations and related workflow. As well each case highlights Synergy’s focus – and success – on mitigating any effects of, the stresses of organizational change on client employees.
Highlighted in SGIT Case: Warehouse Operations is a BPR engagement Synergy performed which resulted in more effective and efficient Sales and Warehouse Operations as well as increased customer satisfaction. As discussed in SGIT Case: Membership Services, Synergy radically re-engineered the Membership Services function of a top International Labor Union over two engagements.

Database Engineering & Administration
Synergy’s Engineering and Administration services are focused on relational database management system (RBDMS) products and tools. Currently, we do not provide support for NoSQL or geospatial based products.
RBDMS products supported comprise commercially available products such as Microsoft SQL Server, MS Access, Oracle, and IBM’s Informix as well as open-source solutions including MySQL, Maria DB, and Postgre SQL.
Database Engineering. Our DB Engineers’ mastery of skills necessary to properly design relational databases would enable each to produce a detailed layout using only a whiteboard. However, their knowledge and use of available RDBMS design tools enables each to leverage such resources to consistently produce excellent designs which provide the foundation necessary to support excellent solution focused systems.
Synergy’s seasoned engineers are adept in developing table design schemas which reduce redundancy and improve data integrity through normalization; at the same time, most have seen those rare cases in which redundant fields are desired. Further, each is skilled in establishing comprehensive table constraints necessary to enforce referential integrity and maintain tightly bound table relationships. As importantly, their expertise ensures business logic is properly integrated through the use of constraints and triggers to establish built-in infrastructure logic.
To further ensure data integrity, we establish primary indexes through appropriate use of multiple fields where possible as opposed to through use of an auto incremented id. Finally, each of our engineers is skilled in API design and development a necessary component of a system pipeline.
Synergy’s focus on database security has grown over the past 20 years commiserate with the significant increase in the risk of data breech. RDBMS and server tools have been adequate to address the security, privacy and compliance requirements of our clients to date. Should that functionality not be sufficient to address a particular client’s needs, we will ensure appropriate third-party products are employed by one of our trusted partners.
Our usual approach is to work with our client’s team to establish security protocols on the frontend which drive the design process to ensure enforcement of each component at a granular level. For example, at the table design level, we user table views restrict access to sensitive columns either limiting access (e.g. select only) or excluding access entirely.
In addition to performing RDBMS dependent roles in Systems Design, Systems Implementation, and Post Implementation Administration, our DB Engineers have also served as members of cross-functional teams performing roles in support of technology independent functions. Specifically, an understanding of business objectives and operations enables their skillset to be employed in the areas of strategic business planning, data modeling, and process modeling.
It is our standard practice to ensure the highest level of password security; in doing so we will use tools such as Oracle’s built-in checkpwd to identify weak passwords as well as account lockout features to reduce the risk of brute force attacks. Additionally, we work with our client’s team to understand access requirements of each user or user group and subsequently grant access on a “need to know” basis. Where use of data-level roles has been appropriate, Synergy has established strong authentication protocols first setting up database roles/groups with pertinent access permissions and subsequently assigning users to those roles/groups through Windows Server Active Directory. Additional security measures are enforced through our database administration services.
In addition to performing RDBMS dependent roles in Systems Design, Systems Implementation, and Post Implementation Administration, our DB Engineers have also served as members of cross-functional teams performing roles in support of technology independent functions. Specifically, an understanding of business objectives and operations enables their skillset to be employed in the areas of strategic business planning, data modeling, and process modeling.

Database Administration. A key responsibility of our Database Administrators (DB Administrators) is to maintain security measures whether put in place by our team as outlined above or established by others. Each follows established protocols when making changes such increasing permissions to existing users/groups or adding new users.
Additionally, through our services we adhere to enforcement of the adage patch early, patch often with regard to database products and tools. To the extent necessary we impress upon appropriate client team members the critical need to operating system and server patches within 24 hours of their release. Working with our client’s team, our DB Administrators ensure timely system and database backups are made. Finally, when tasked to do so, we design and enforce regular data audits.
Synergy's Expertise In The Fields Of Data Cleansing & Conversion
Synergy’s senior management have solid business backgrounds in finance and operations. Each have MBA’s. Early in his career, our VP of Operations worked as a Certified Public Accountant for KPMG first as an auditor and later as a business consultant. It follows that a substantial majority of our Data Cleansing (Cleansing) and Data Conversion (Conversion) engagements have been focused on accounting, finance, and billing related systems. Over 30+ years, we have been engaged to convert systems across a variety of different platforms. Our experience and expertise in the fields of cleansing and conversion is both deep and varied.
Roughly two-thirds of custom systems engineered by Synergy have been developed to replace legacy systems. Furthermore, a number of those have required integrating two or more standalone legacy systems that had grown organically to meet the needs of organizational silos developed around departments or locations. By definition, such independent units do not share resources and most often use different coding schemes and methods to describe data.
Quite a few legacy systems our team has been engaged to replace were developed by one or more power users utilizing available tools such as MS-Access as a first step towards automation; such development efforts are often necessitated by an inability to draw necessary IT attention and resources to meet departmental needs. These systems often contain data which exhibits most, if not all, of the error conditions typically discovered over the course of a cleansing project.
Those unfamiliar with details of cleansing and conversion will benefit from Cleansing/Conversion: A Primer.
Data cleansing consists of two sub-disciplines Data Profiling (Profiling) and Data Scrubbing (Scrubbing). Below is outlined the approach our teams take when profiling and scrubbing. The final section details out approach to conversion engagements.
Profiling. At the onset of every profiling engagement, Synergy defines the universe of possible error conditions based on criteria derived from the study of the source data structure. Additionally, when cleansing is performed as a component of a conversion, we perform a methodical study of the target data structure. Our examination is focused on the schema of each table which defines constraints that in addition to data type include: range limitations, discrete value list restrictions, prohibition on null or empty values, foreign key constraints, unique key requirements, and primary key specifications.
When performing a legacy conversion, we often find both numeric and date values stored in text fields. Our experience has shown that importing all raw data into text fields reduces errors otherwise likely to be encountered. Synergy sets up staging tables necessary to support cleansing in the target environment.
Our profiling processes discover values contained in such text fields which are not valid given the data type of the target field are identified. Further, we identify values that are the correct data type but lie outside of the specified acceptable range. We also log fields which are empty in violation of constraints applied to the corresponding field in the target database.
Our analysts study legacy file layouts and data patterns to identify foreign key candidates. A unique listing of values is composed for further evaluation. The Team’s study of data underlying standalone systems may reveal use of different coding schemes for the identical primary record. For example, one system may identify a customer using only numeric digits while another uses the first three letters of the customer’s name followed by numeric digits. In consultation with our client, we develop an agreed upon coding scheme and setup mapping tables to facilitate conversion of legacy coding.
It has been Synergy's practice to postpone identification and elimination of duplicates and perform that process as final step of scrubbing; likewise, we have found that determination of mutually exclusive or contradictory data is best similarly deferred.

Scrubbing. Synergy consistently employs a conservative strategy when scrubbing data; to that point we setup parallel staging tables into which corrected rows are written thus ensuring original values are not lost. Anomalies are logged for easy reference and resolution.
We insert placeholders in lieu of invalid numeric or date values until such time as the correct date can be determined through research. For example, a legacy date value of 02/30/1965 would be logged and replaced with 12/31/2999. Placeholders are also used to populate fields constrained to prohibit null or empty data.
Valid numeric or date values determined to be out of a specified range are logged but written as found. This practice is made to accommodate clients that choose to convert out of range data as found in order to expedite system cutover; in such cases, data field range constraints are removed while keeping user entry edits thus permitting anomalies to be researched and corrected post-cutover. (In such cases, a final scrubbing of production data is done after all errors have been addressed at which time data field range constraints are restored.)
Synergy places emphasis on validating foreign keys against the corresponding primary key table to ensure a smooth conversion. Orphaned rows are logged; as appropriate, a dummy record will be inserted into the primary table to permit scrubbing to move forward while further research is done.
In the final stage of scrubbing, Synergy identifies and logs duplicate data before making corrective deletions. Additionally, we determine and log instances of mutually exclusive or contradictory data. As an example of mutually exclusive data within the same record, it is not uncommon to find city and state values that do not comport to the corresponding zip code value.
Finally, to discover contradictory sequencing across a series of rows, Synergy builds validation tables based on a study of an organization’s business rules. Contradictory row sequencing is found when business rules dictate the universe of key-field values permitted in the row following another given the key-field values in the predecessor row. For example, in a Union Membership system Member Status History table a given row coded to designate an individual’s membership as suspended can be followed only by one coded to indicate 1) that the membership was re-instated, 2) that the membership was forfeited or 3) that the suspension record was cancelled as having been erroneous. Any other value would constitute a row sequencing error.
Conversion
Synergy well understands that a successful conversion is critically dependent upon having clean data. Equally important is having a target database engineered to detailed specifications drawn from the work of competent systems analysts and systems designers.
Over ninety-five percent of Synergy’s conversion engagements have included responsibility to perform cleansing to ensure underlying data is of the highest quality. Additionally, the vast majority of target databases had been engineered by Synergy specialists; the remainder were a component of a proven commercially available accounting or operations systems.
Our portfolio of database conversions has spanned a number of industry segments in the Commercial space as well as in the not-for-profit arena. The types of systems converted have been equally wide-ranging to include:
Operations & Support:
- Warehousing
- Scheduling
- Defined Benefits Pension Plans
- Membership
- Sales Order & Fulfillment
- Inventory
- Human Resources
Accounting & Finance:
- General Ledger
- Payroll
- Accounts Payable
- Accounts Receivable
- Job Costing
The discussion which follows requires a reiteration of the difference between conversion and migration. Conversion processes involve transforming clean data before writing it to the target database. Migration, on the other hand, is a much simpler process limited transferring data from a source database to a target database having essentially the same structure.
Synergy has successfully provided both conversion and migration services. The above specificity is made to provide context to our selection of tools for each of these distinct processes.
Synergy customizes and tailors its conversion tools for each specific conversion engagement. Doing so is required to accommodate transformations such as changes to coding typically necessitated on integration projects. When performing migration services, we use component toolsets of the target database. In past migrations to a MS SQL Server platform, for example, we have used either the Transact-SQL based BULK INSERT command or the SSIS (SQL Server Integration Services) toolset.
Underlying our approach is a clear understanding of the specifications on which cleansing is to be performed. Documentation of properly performed scrubbing processes will provide an understanding of the business rules and specifications upon which the target database has been built. In the rare instances in which such documentation is not available, we would perform a comprehensive review of the database structure to build in-depth knowledge of all table constraints.
Both converting and migrating data into a target database require identifying table relationships to segregate each into one of four categories:
- one-to-one primary tables having no foreign keys
- one-to-one primary tables with foreign keys
- one-to-many tables which by definition have at least one foreign key
- many-to-many tables which by definition have two foreign keys
Such segregation provides the order in which development target tables are populated. Any errors which surface are addressed and resolved before the next group of tables is loaded.
For both conversion and migration projects, Synergy confirms that all data is correctly written to target tables. Record counts are verified. Additionally, hash totals are used on key fields to verify that target data is identical to its source.
Synergy has had great success performing both conversion and migration services. Our consistent ability to provide positive results in each arena is directly attributable to a conservative engineered approach to each engagement.

Programming & Scripting
Synergy has provided Programming services to clients spanning numerous commercial market sectors, pension plans, international labor unions and not-for-profits for over thirty years. Our support of scripting languages dates to the firm’s broadening of its service offerings to include development and support of web pages and web services.
Uses of the term programming languages which follow are intended to include interpreted scripting languages.
Our project engagements in this critical field are limited to those committed to strict adherence to the best practices of Software Engineering. More specifically, we will not commit programming resources to development undertakings not built upon standards that ensure a systems design of the highest quality; doing so would be contrary to our commitment to the underlying principles of Software Engineering.
In both agile and traditional environments, we believe that assigning an individual programmer to a given task – as opposed to employing paired programming model – produces the most effective results. Each programmer is complemented by a team member responsible for unit testing and peer review. All are expected to use best practices with an emphasis on code readability both to facilitate peer review and to support further enhancements or required modification.
Within the vast array of programming platforms, our team is focused on those appearing in the word cloud at right. The programming and scripting platforms having the strongest emphasis are those with which our team has worked with most often. We rely on our trusted IT partners to deliver expertise in some including Ruby and Rails. When using an IT partner to support our team, Synergy takes responsibility for all aspects of the roles to which external resources are assigned.

Implementation Management
Over a 30-year period, Synergy’s implementation engagements have run the gamut from straightforward to complex. The variation in degree of difficulty has been driven by the breadth of system functionality as well as by the number of client departments, and team members within each department, impacted by the software (the footprint).
Further, differences have been influenced by the type of system being installed. Procedures employed vary depending upon whether the system is a newly developed software application, a major enhancement to an existing application, or a third-party vendor software package.
The scope of responsibility has differed across projects. For example, the task of production testing of various features and outputs has fallen under the purview of a small number of projects. Similarly, a small number of third-party software implementation engagements have included responsibility for configuration of standard features and for customization of features necessary to meet an organization’s specific needs.
Our approach to each engagement has been shaped through use of a proven framework to ensure the most effective and efficient rollout possible.
Outlined below is the approach that Synergy employs on implementation engagements. Components of this framework are selected, greater emphasis given to some, based on the footprint of the system within the organization and on the type of system being installed (e.g. newly developed, major enhancement, third-party). Through our approach we endeavor to:
Ensure Adequate Project Support. Success of any software implementation initiative is directly dependent on support of management and of other key stakeholders. In fact, other than the degree to which a system meets an organization’s needs, such support is the most critical element to achieving good outcomes as it directly impacts the quality, and autonomy, of the implementation team. As well, it drives the degree to which the team is supported by others, both internal and external to the organization.
Two factors greatly influence how critical such support is to the achievement of a positive outcome. Those components are: 1) the number of departments and team members impacted by the project; and, 2) the degree of resistance to change within the organization.
Prior to accepting an implementation engagement, Synergy evaluates the footprint of the proposed rollout vis-à-vis the organizational culture. A larger footprint and higher degree of resistance demand increased support from higher levels within the entity. Absent critical support of management and key stakeholders commensurate with the degree of risk posed by these factors, Synergy declines such engagements as the probability of a positive outcome will be significantly diminished.
Perform Comprehensive Planning at the Onset. Our consistent success has been guided by front-end planning to ensure prerequisites are met and to ensure potential pitfalls are addressed thus minimizing impact on engagement objectives. We ensure that there is clear definition and a consistent understanding of:
- deliverables and expected outcomes which define project scope. This includes a broad understanding of system functionality (derived from the development phase, or software selection phase, as appropriate)
- items or issues specifically excluded from the project definition so as to reduce the risk of scope creep as the project progresses
- the project timeline as well as the proposed starting and ending dates. Constraints prohibiting extension of the ending date beyond that proposed must also be known
- the project budget and available resources comprising IT physical assets and personnel, outside contractors, and, where appropriate, third-party software personnel resources
- potential conflicts which may exist whether internal or external to the organization
- the project impact on internal departments and team members as well as on external parties to include the organization’s customers, its vendors, and governmental entities
- potential obstacles of any nature
Assemble a Cross-Functional Team. A team tailored to the type and footprint of an implementation is critical. Resourcing the appropriate skillset is necessary to ensure all necessary roles are filled with competent resources whether each is internal or external to the entity. To the extent possible we attempt to draft individuals who have participated in the software development or, in the case of third-party software, the selection process.
Without regard to the system footprint, we seek to assemble a team that collectively can fine-tune and deepen the implementation plan, can promote communication among stakeholders, can promote user buy-in, and, more importantly can address and resolve problems quickly. Such individuals include agile product owners or internal champions placing an emphasis on knowledge of system functionality and good communication skills. The team must also include technical resources who either participate directly with installation and related issues or serve as a critical liaison to internal IT resources.
An ideal team is truly cross-functional with the experience and collective skillset to support an aggressive approach when course correction is necessary. Again, depending upon the footprint, it includes resources experienced in change management. (See Change Management below). Our team building process includes an iterative evaluation to discover and address talent gaps as required.
Ensure Sufficient Communication with all Stakeholders. Adequate communication with users regarding upcoming changes in workflow is a necessary component of each implementation project. We ensure that impacted users and stakeholders have a clear understanding of project objectives and expected benefits early in the process; as well as each user is provided an in-depth understanding of the degree to which their workflow and/or role will be impacted.
We employ appropriate mechanisms to elicit user feedback starting with their training and continuing through post-implementation review.
Finally, we ensure the team provides immediate feedback to the software development team, or third-party support resources, regarding failure of the software to meet defined needs and system objectives.
Address Change Management. Implementation is often defined as the process of adopting and integrating a software application into an organization’s systems and workflows. That definition falls short, however, with regard to recognizing that changes in workflow will be required with the rollout of virtually all applications – whether developed in-house or purchased/leased from a vendor. Synergy’s front-end planning, and resulting implementation procedures, address the need for change management through structured methodologies to increase employee adoption and usage of the software. The more expansive the implementation footprint and higher the degree of integration of a rollout, the more emphasis we apply to this critical aspect of the implementation phase.
Adequately Train Users and Support Resources. Synergy ensures an appropriate level of training is available and is achieved . It is critical that users and support resources (such as help desk personnel) are afforded uninterrupted time in which to be trained.
We have rarely found off-system training using fictitious data to be effective or efficient. When appropriate, we train the system running in a test environment using data extracted from the production environment. As to be expected, larger and more complex projects require use of a Train-the-Trainer model. Conversely, on smaller, less complex engagements, we have found training uses post-cutover to be the most efficient and effective approach.
To the degree possible we schedule training parallel with other implementation tasks. Our experience has shown that users benefit from a high-level understanding of all essential functions including, where appropriate, those in the domain of another department or business unit.
Users are instructed where to turn for help post-implementation typically to a call center or to a power user within their department or business unit. When tasked to do so, we ensure training on new features or enhancements is made available as future releases are rolled out. Finally, we ensure mechanisms remain in place to elicit user feedback.
Managing Installation and Integration. The vast majority of Synergy’s implementation engagements have included conducting oversight of software installation in the production environment. As well most include responsibility for oversight of legacy migration data and for ensuring its validity through verification of record counts, use of hash totals, etc.
Synergy develops a cutover plan for each implementation engagement and refines that plan as necessary over the course of the project. Where practical we work in consultation with the development team to parallel the new system in a test environment for one cycle, typically a month for accounting and finance applications, using data extracted from production tables. As noted above, this practice permits user training based on real data.
Where possible we initiate a phased rollout using software bridges from existing systems as necessary. Rollout of minimum viable product in iterative releases is always preferable as doing so reduces risk significantly.
We ensure employees are notified as to cutover timing as far in advance as possible to avoid conflicts including outside commitments and scheduled vacations. Finally, rollouts are conducted off-hours to minimize disruption and downtime.
Ongoing Support Resources. To place additional emphasis on this important aspect of implementation, Synergy ensures users have effective support available on a timely basis both during cutover and post-implementation. As noted previously, resources must be dedicated to support implementation particularly as required to address errors or omissions noted throughout the rollout of internally developed software. In the case of third-party software, vendor resources must be available on a timely basis to resolve issues with configuration, customization, and integration with other systems.

The Consortium for Information & Software Quality (CISQ) has estimated the total Cost of Poor Software Quality (CPSQ) in the US for the year 2020 to have been $2.08 trillion; of that amount, CISQ estimated that “unsuccessful development projects” account for $260 billion of that total.
CISQ data is not broken down to separate unsatisfactory outcomes due to inadequate or poor design versus resulting from poor implementation planning and execution. Subpar implementation outcomes often result in software not being used to its full potential; as well as it may give rise to unexpectedly high costs incurred yearly subsequent to implementation. Consequences of both adversely impact – or altogether negate - return on investment.
The risk of implementation failure extends beyond calculable sunk costs. It can result in distrust of other IT systems among stakeholders within the organization. Skepticism regarding system outputs will unquestionably contribute to a decrease in revenue and/or an increase in variable costs.
Oriola, a pharmaceuticals and healthcare products firm operating in the Nordic countries, suffered damage to its reputation in 2017 due to failure of its Enterprise Resource Planning (ERP) system implementation.
Catastrophically, implementation failure may impair an organization’s ability to succeed within its market. For example, Target suffered a more dramatic loss after it implemented an SAP ERP system to support its expansion into the Canadian market; the new system was rolled out to replace a legacy system used in the US. After three years of effort to correct issues with the system - which included a complete collapse in its supply chain - the firm pulled out of the Canadian market altogether.
A properly structured implementation supported at the highest levels of Oriola would have uncovered flaws in the design of its ERP system prior to final cutover. Likewise, an autonomous cross-functional team having adequate communication to capture user feedback would likely have uncovered critical flaws in Target's attempt to implement SAP's ERP software; whether crippling issues were due to misconfiguration or to a poor fit for the organization when the issues arose the magnitude should have been ferreted out and addressed. Well-staffed implementation teams, supported at the highest levels of an organization, can significantly blunt the financial impact of a poor software development process, or of poor package selection, by unearthing significant problems before an ill-advised go-live decision is made.